During the weekends, I am usually exploring targets for bug bounty; however, this time I thought of securing Indian cyber space. I had a target in mind. it was Akasa Air. The Airline started its flight operations on the same day, 07th August 2022. I thought of looking into it in July, but I decided to wait till they commence flight operations, as it could open more attack surface and generate some interesting data.
I am interested in aviation security after hacking into United Airlines multiple times and receiving a lot of air miles as a reward.
As part of recon process, I explored domains, subdomains, Internet-facing IT infrastructure of Akasa Air, then I noticed their registration page. A functionality on akasaair.com where users can create a profile by submitting their name, phone number, Email etc. I created my profile.
After creating my profile, I logged into it and searched for my own PII in burp responses. I found an HTTP request which gave my name, email, phone number, gender, etc. in JSON format. I immediately changed some parameters in request and I was able to see other user’s PII. It took around ~30 minutes to find this issue.
I initially tried to reach out Akasa Air via Twitter DM asking for an email, they responded with an email address ([email protected]) , I asked again for an email address of a security person because generally the generic emails are handled by customer support staff which are possibly third-party vendors.
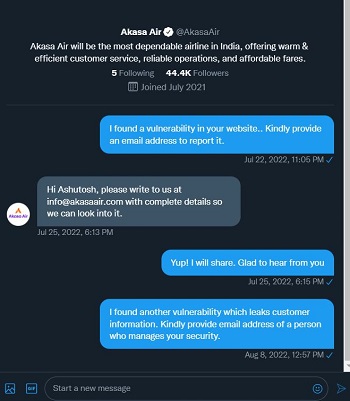
I sent an email to [email protected] and requested a different email address of someone from their security/IT team but received no response.
I reached out to Jagmeet Singh from TechCrunch to check if he can find someone from Akasa Air who would look into this issue on urgent basis, as he helped me reaching out to shipyaari team a few weeks ago.
https://techcrunch.com/2022/08/16/shipyaari-customer-data-exposed/
Akasa fixed the issue within two weeks. In case you registered on their website, you need to understand that there is a possibility that I am the only one who found this vulnerability and it was not found, exploited by threat actors. in this case, there is no need to panic.
I appreciate expedited action on this issue by Akasa Air. They also informed their customers and CERT-In about the incident. This is something new when it comes to security incidents in Indian companies. I wish them all the very best in their journey.



